The main method for distribution of AnVi.FakeCog is by exploits that take advantage of a vulnerability in applications that use .pdf format files.
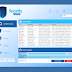
AnVi.FakeCog uses the rather unimaginative name “Antivirus” on its graphic interface:
 (Click on graphic to enlarge)
(Click on graphic to enlarge)The AnVi.FakeCog installer looks like this:
 (Click on graphic to enlarge)
(Click on graphic to enlarge)A machine infected with AnVi.FakeCog shows the following files:
 (Click on graphic to enlarge)
(Click on graphic to enlarge)Files and directories installed:
c:\Program Files\AnVi\
c:\Program Files\AnVi\about.ico
c:\Program Files\AnVi\activate.ico
c:\Program Files\AnVi\avt.db
c:\Program Files\AnVi\avt.exe
c:\Program Files\AnVi\avtext.dll
c:\Program Files\AnVi\avthook.dll
c:\Program Files\AnVi\buy.ico
c:\Program Files\AnVi\help.ico
c:\Program Files\AnVi\scan.ico
c:\Program Files\AnVi\settings.ico
c:\Program Files\AnVi\splash.mp3
c:\Program Files\AnVi\Uninstall.exe
c:\Program Files\AnVi\update.ico
c:\Program Files\AnVi\virus.mp3
%UserProfile%\Application Data\Microsoft\Internet Explorer\Quick Launch\Antivirus.lnk
%UserProfile%\Desktop\Antivirus Support.lnk
%UserProfile%\Desktop\Antivirus.lnk
%UserProfile%\Desktop\nudetube.com.lnk
%UserProfile%\Desktop\pornotube.com.lnk
%UserProfile%\Desktop\spam001.exe
%UserProfile%\Desktop\spam003.exe
%UserProfile%\Desktop\troj000.exe
%UserProfile%\Desktop\youporn.com.lnk
%UserProfile%\Local Settings\Temp\wmsdk64_32.exe
%UserProfile%\Local Settings\Temp\wscsvc32.exe
%UserProfile%\Start Menu\Programs\AnVi\
%UserProfile%\Start Menu\Programs\AnVi\About.lnk
%UserProfile%\Start Menu\Programs\AnVi\Activate.lnk
%UserProfile%\Start Menu\Programs\AnVi\Antivirus Support.lnk
%UserProfile%\Start Menu\Programs\AnVi\Antivirus.lnk
%UserProfile%\Start Menu\Programs\AnVi\Buy.lnk
%UserProfile%\Start Menu\Programs\AnVi\Scan.lnk
%UserProfile%\Start Menu\Programs\AnVi\Settings.lnk
%UserProfile%\Start Menu\Programs\AnVi\Update.lnk
Registry changes:
HKEY_CURRENT_USER\Software\Malware Defense
HKEY_CURRENT_USER\Software\Paladin Antivirus
HKEY_CLASSES_ROOT\CLSID\{5E2121EE-0300-11D4-8D3B-444553540000}
HKEY_LOCAL_MACHINE\SOFTWARE\AnVi
HKEY_LOCAL_MACHINE\SOFTWARE\Malware Defense
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Antivirus
HKEY_LOCAL_MACHINE\SOFTWARE\Paladin Antivirus
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Antivirus"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "wmsdk64_32.exe"
How to remove AnVi.FakeCog:
If AnVi.FakeCog has infected your pc, you should remove it immediately. Click here to use VIPRE to remove AnVi.FakeCog from your computer now.









you know, The writers of 'AnVi' didn't encrypt a piece of code
ReplyDelete